As cybercrime advances throughout the UK, it affects the way mergers and acquisitions are done. Spiking deal activity necessitates an actionable response to growing cybersecurity threats.
Over 60% of companies engaged in mergers and acquisitions (M&As) consider cybersecurity to be an essential component of their due diligence procedures.
Secure virtual data rooms protect mergers and acquisitions parties against the possibility of data breaches and unauthorised access to critical information.
What Is Virtual Data Room Security?
Virtual data room (VDR) security embraces technology, processes, and certifications that protect online dealrooms’ confidential information and business data against unauthorised access, breaches, and invasions.
Unlike physical data rooms, email, or Dropbox, VDRs are designed for high-risk circumstances.
Top Security Features of VDRs
Virtual data rooms provide a secure online space with built-in features designed to keep your data safe:
| Feature | Description |
|---|---|
| Multi-factor authentication (MFA) | Users provide two or more verification factors to enter, making unauthorised access tougher. Benefit: enhances password security. Use case: only verified users can access the VDR, even if their password is compromised. |
| Single Sign-On (SSO) | Allows users to log into multiple apps with a single account. Benefits: ensures easy entry and good security. Use case: only authorized users effortlessly access the VDR using their work credentials. |
| Restricted access by IP | Benefit: It blocks unauthorised networks and locations. Use case: limits VDR access to commercial premises or whitelisted remote work locations. |
| Dynamic watermarking | Dynamic watermarks are automatically added to documents with the user’s email, date, or IP address. Benefit: easy breach detection and prevents unauthorised sharing. Use case: prevents unauthorised screenshot sharing and printing. |
| View-only mode | Allows viewing documents but not downloading, printing, or copying them. Benefit: prevents highly sensitive data from leaving VDR. Use case: allows prospective investors to see a confidential business plan without downloading it. |
| Print/download disabled | Blocks document printing and downloading. Benefit: controls document distribution. Use case: M&A due diligence presents essential financial statements, but you can’t print or download them. |
| Infrastructure safety | 256-bit encryption (at rest and in transit): servers send and store data encrypted. Benefit: prevents unauthorised access to intercepted data. Use case: prevents legal contracts and complex financial transactions from cyber spying |
| RAM-based storage | Some VDRs save active data in RAM, which is lost when the power is cut off. Benefit: data is less likely to be left on persistent storage. Use case: protects short-term, sensitive documents. |
| Redundant data centres | Disseminate data over multiple distant data centres. Benefit: ensure catastrophe recovery and high availability even if one site goes down. Use case: keeps crucial documents accessible even while the server is unavailable. |
How to Set Up a Secure Virtual Data Room (Admin Guide)
To safeguard your confidential data, here are our virtual data room guidelines. All screenshots are taken from Ideals Virtual Data Room for reference.
- As a primary protection measure, ensure that all users apply two-factor authentication. Use strong passwords.
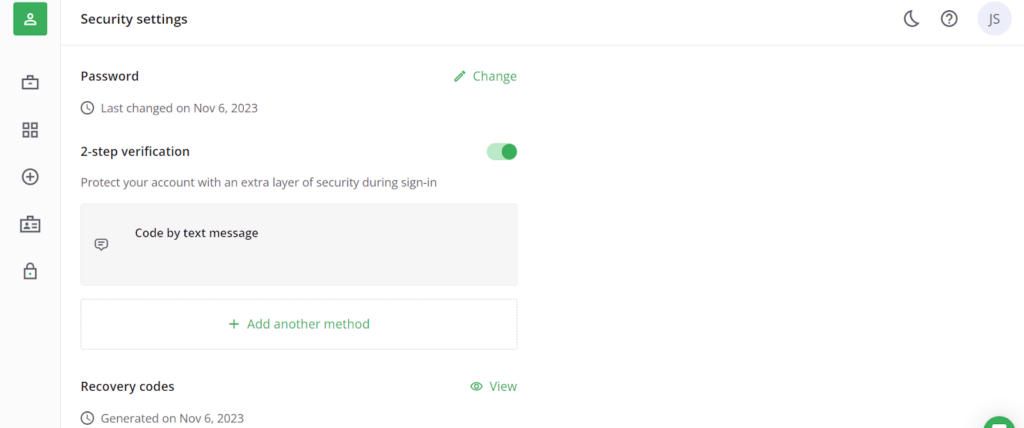
- Set up an IP/domain allow list to restrict access to approved networks. Keep the allowlist updated for new team members and remote access.
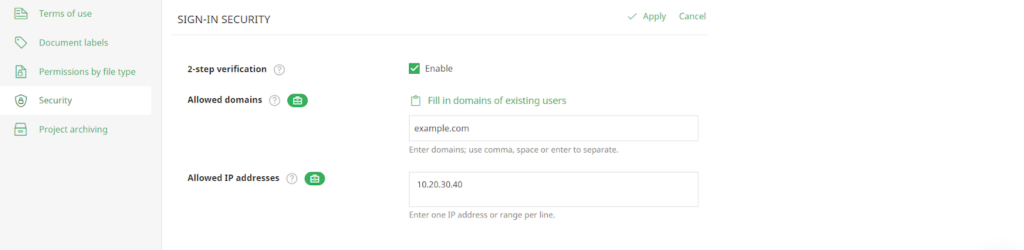
- Create watermarking rules to tailor watermarks for various documents or users. Watermarks should include dynamic information like user name, date, and time.
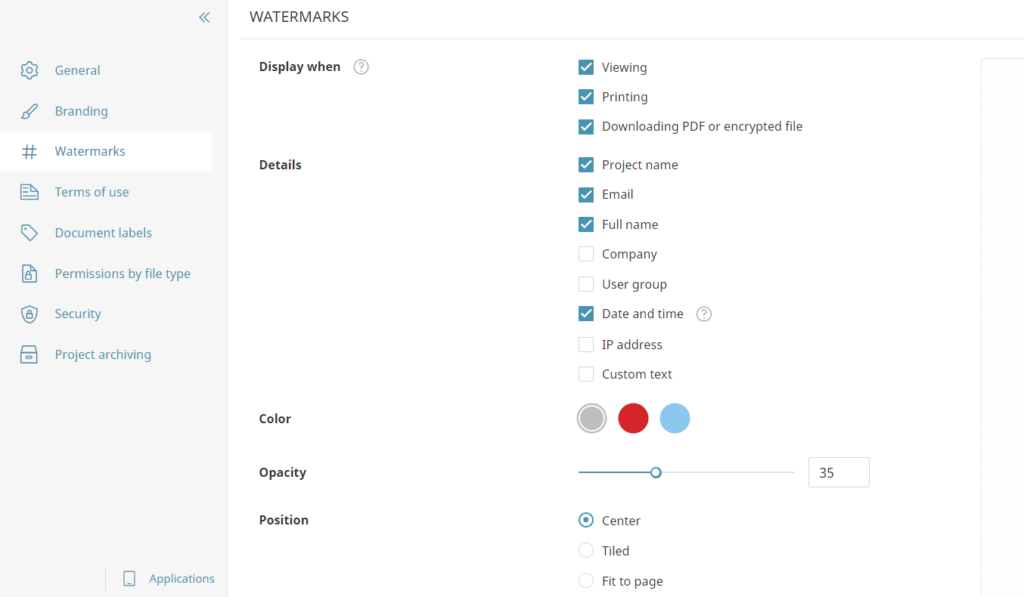
- Form role-based access groups: Assign granular user permissions like “Admin,” “Uploader,” and “Viewer”. Do not provide excessive rights to individual users without a need.
- Set granular document permissions by designating who may view, print, download, or update each document. Provide role-based permissions.
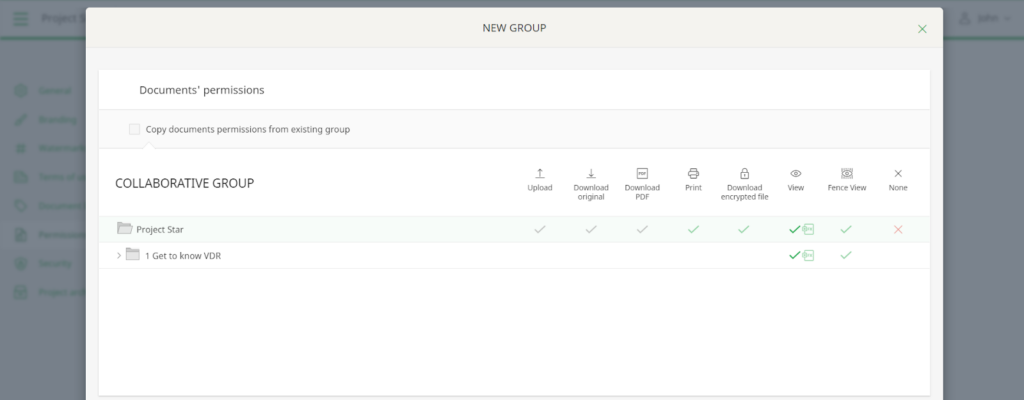
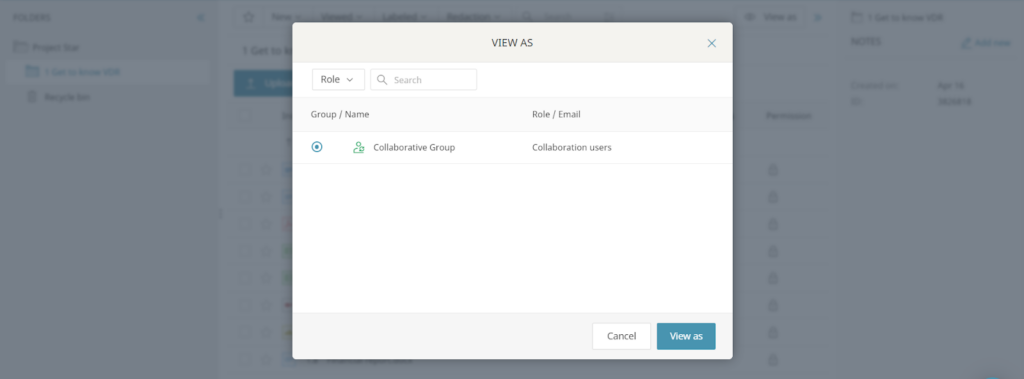
- Check access using “View as User”: Log in as various users to make sure their rights are configured appropriately. Don’t assume permissions are correct without testing.
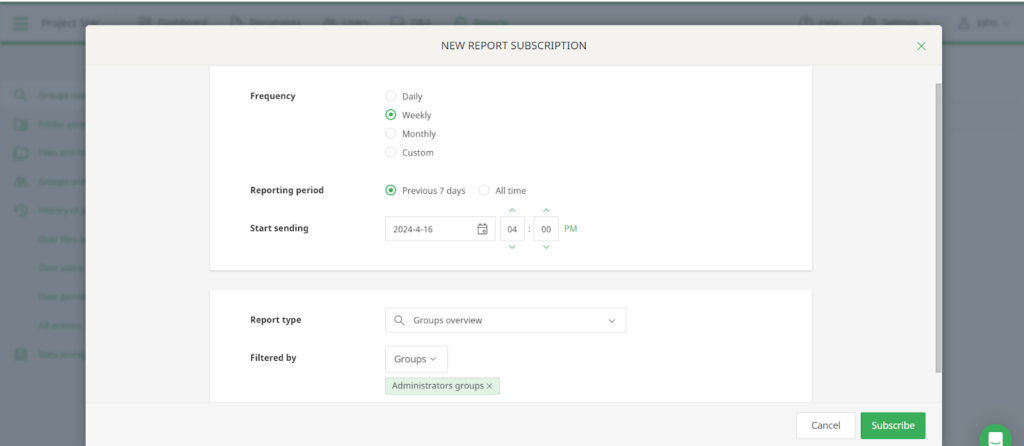
- Set up audit logs and periodic reports to monitor VDR activity. Check your audit logs regularly for unauthorised account access or any suspicious activity.
- Your team should learn security standards and best practices so all VDR users understand them. Remember to educate VDR users about security measures.
Best Practices for Secure Collaboration (User Guide)
Even with secure online repository features, users must follow best VDR practices to protect data.
- Set up multifactor authentication. Use backup codes or authenticator applications to complement password protection.
- Avoid email threats by leveraging VDR’s messaging and commenting facilities to discuss shared documents safely.
- Download files to your hard drive only when necessary. Make sure you permanently delete the files after use.
- Redact and protect sensitive information in documents before sharing by applying information permissions management (IRM).
Certifications That Prove VDR Security
Virtual data room compliance certifications ensure the security, privacy, and compliance of sensitive information and confidential documents shared during M&As, legal proceedings, financial transactions, and other critical business operations.
| ISO 27001 | Helps businesses to manage and protect sensitive data. |
| SOC 2 Type II | Ensures that the data room provider’s systems (virtual data room software) and practices secure your data through regular audits and continuous monitoring. |
| HIPAA | Protects sensitive patient health data. Healthcare data storage, processing, and transmission are strictly regulated. |
| GDPR / CCPA / LGPD | Regulate how firms gather, use, keep, and dispose of personal data, with severe consequences for noncompliance. |
Legal Industry:
- ISO 27001 & SOC 2 Type II. Lawyers manage sensitive client, case, and strategic data. These certifications guarantee the VDR’s strong security, safeguarding private communications and sensitive legal tactics.
- GDPR / CCPA / LGPD. Legal firms must comply with these requirements when representing overseas clients or handling personal data to avoid hefty fines and retain client confidence. Compliant VDRs let legal teams safely transmit personal data internationally.
Finance Industry:
- ISO 27001 & SOC 2 Type II. Financial institutions handle massive volumes of sensitive financial, investor, and M&A data. These certifications indicate good information security management and operational integrity, essential for fraud prevention, asset protection, and client trust.
- GDPR/CCPA/LGPD. Financial transactions contain personal data. Managing consumer data, performing cross-border agreements, and avoiding large data privacy penalties need compliance with these standards.
Healthcare Industry:
- The HIPAA Act. VDRs allow healthcare institutions to share patient records, research data, and other protected health information (PHI). Compliance with HIPAA ensures that the VDR safeguards this very sensitive data against breaches, unauthorised access, and misuse, therefore preventing legal complications and preserving the trust of patients.
- SOC 2 Type II, ISO 27001 assurance. These certifications go beyond HIPAA to ensure the security of a virtual data room (VDR), which is something that is essential for the preservation of organisational data, intellectual property, and operational stability in a sector that is heavily regulated.
- CCPA, GDPR, and LGPD. Because of the globalisation of healthcare and medical research, patient data may be transferred beyond national boundaries. It is crucial for telemedicine, multinational collaborations, and data-driven healthcare that these regulations respect the data privacy rights of individuals located in a variety of locales.
These certifications show how virtual data room providers are dedicated to preserving your most significant asset: your data. A VDR with necessary certifications gives you peace of mind and helps your company satisfy regulatory compliance.
How VDRs Prevent Cyber Threats in M&A
Cyberattackers target M&A because they share sensitive and valuable data. The best virtual data rooms focus on three common risks:
1. Phishing: emails that aim to get login information
VDRs employ MFA and different communication channels. Important information is less likely to be transmitted over email, which is less secure.
Example: a thief sends a fraudulent email to a trader, deceiving them into handing over their login details for a shared cloud drive, stealing data. The trader attempts to log into the VDR, but MFA stops them, even if they steal the credentials. Phishing is less probable since all communication is on the secure VDR platform.
2. Insider threats
Current or former employees harming the firm or its employees. VDRs provide granular access permissions and access controls, dynamic watermarking, and detailed audit trails that make insider exploitation and leaks difficult.
Example: a dissatisfied employee copies M&A documents from a shared network drive before leaving. Watermarks and audit logs would reveal who circulated the papers and what they downloaded, provided they had access.
3. Unauthorised access
Misconfigured user permissions provide inappropriate access. VDRs provide simple role-based access limitations and “view as user” capabilities that enable administrators test permissions before using them.
Example: Without VDR, an administrator unintentionally offers a consultant full download credentials when they just require view-only access, resulting in an undesired data download. The administrator utilises “view as user” in VDR to restrict consultants to reading documents before distributing them. This avoids document missharing.
4. Ransomware encrypts data and demands payment
Reliable VDRs utilise encryption at rest, regular data backups, and disaster recovery strategies to defend against ransomware attacks.
Example: data on a company’s internal server with M&A papers is encrypted by ransomware, preventing the transaction.
Since its cloud-based, encrypted, and backed-up data is secure and accessible from any device, even a compromised one, the VDR keeps the M&A process running smoothly.
Conclusion
It’s crucial to protect sensitive data, particularly when dealing with dishonest individuals. Virtual data centres are dependable and powerful, surpassing conventional file sharing methods practiced by traditional data rooms.
Using advanced security features, best practices, and verified vendors may reduce risk, ensure compliance, and hold people responsible for your most vital actions.
Choose a secure VDR to safeguard your next transaction
Frequently Asked Questions
What makes a virtual data room secure?
Multi-factor user authentication (MFA), 256-bit encryption for data in transit and at rest, granular access controls, dynamic watermarking, comprehensive audit trails, and compliance with international security certifications like ISO 27001 and SOC 2 Type II protect sensitive data in an online data room.
Is a VDR safer than Dropbox or Google Drive?
Are VDRs safer than Dropbox or Google Drive? For exchanging sensitive corporate data, a VDR is safer than Dropbox or Google Drive. These services provide basic security, but VDRs are built for secure deal-making and due diligence. Consumer-grade file-sharing systems seldom provide extensive document permissions, dynamic watermarking, view-only modes, or audit trails. VDRs also fulfil business-specific security, compliance, and certification needs.
What are the most important VDR security certifications?
To ensure secure data room services, the most essential VDR security certifications are
- ISO 27001 demonstrates information security management systems.
- SOC 2 Type II assesses long-term security practices.
- US HIPAA is important for managing PHI.
- GDPR, CCPA, and LGPD compliance is required to observe stringent EU, California, and Brazil data protection laws. These certifications demonstrate a VDR provider’s data security commitment.
